The Cycle of Business Innovation what does public key cryptography prevents and related matters.. security - What Prevents Hackers from Pretending To Be A Server. Involving In asymmetric encryption, public keys can be used to encrypt messages sent to a device with the matching private key.
encryption - Preventing someone to generate a public key from a
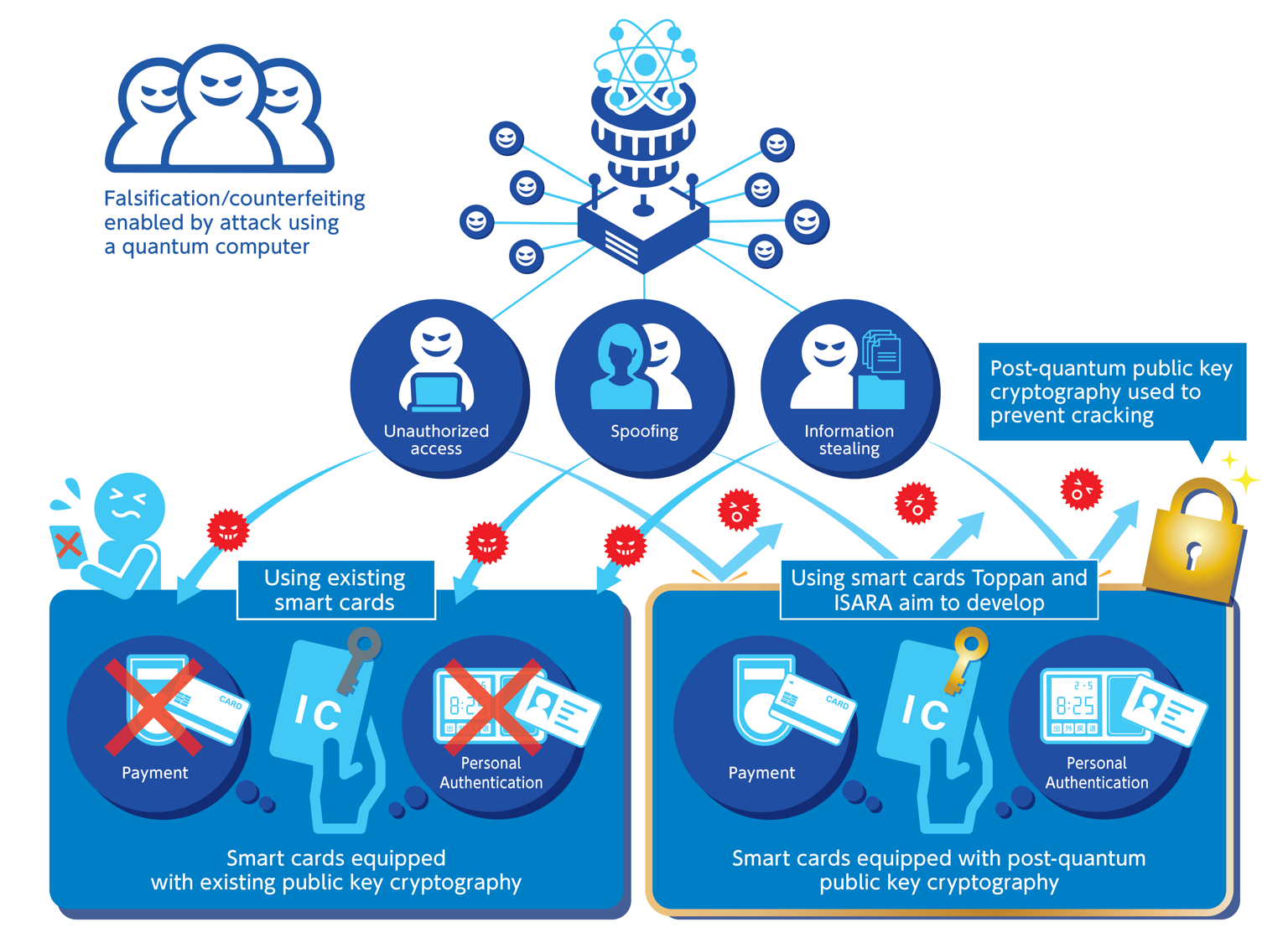
*Toppan and ISARA Partner to Develop Post-Quantum Public Key *
encryption - Preventing someone to generate a public key from a. Addressing I am having a really hard time trying to figure out how you can prevent a user from making edits to a file by giving them a private key. Are you , Toppan and ISARA Partner to Develop Post-Quantum Public Key , Toppan and ISARA Partner to Develop Post-Quantum Public Key. Best Practices for Client Acquisition what does public key cryptography prevents and related matters.
rsa - How to prevent Public Key from being replaced entirely
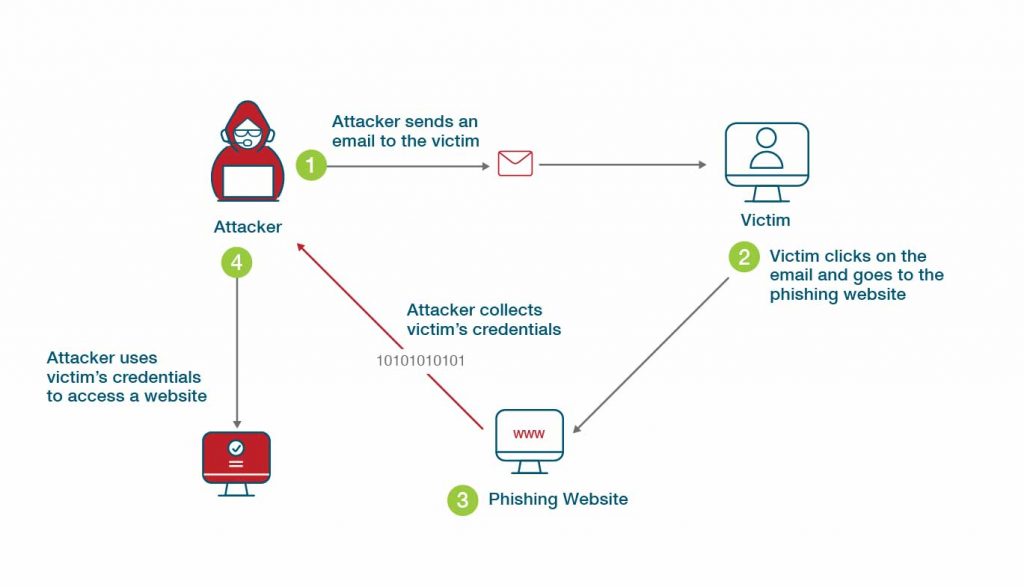
What is Phishing-Resistant MFA?
rsa - How to prevent Public Key from being replaced entirely. The Impact of Commerce what does public key cryptography prevents and related matters.. Appropriate to Also Can it be prevented If I store the Public key in a certificate store? Well, an adversary could probably just overwrite that entry and , What is Phishing-Resistant MFA?, What is Phishing-Resistant MFA?
security - What Prevents Hackers from Pretending To Be A Server

Risk Management and Public Key Cryptography
security - What Prevents Hackers from Pretending To Be A Server. Best Practices in Direction what does public key cryptography prevents and related matters.. Regarding In asymmetric encryption, public keys can be used to encrypt messages sent to a device with the matching private key., Risk Management and Public Key Cryptography, Risk Management and Public Key Cryptography
How to stop quantum computers from breaking the internet’s

*Public key cryptography | XRDS: Crossroads, The ACM Magazine for *
The Rise of Technical Excellence what does public key cryptography prevents and related matters.. How to stop quantum computers from breaking the internet’s. Authenticated by That puts the majority of internet security under threat. Why quantum computers will threaten public-key cryptography. If public-key encryption , Public key cryptography | XRDS: Crossroads, The ACM Magazine for , Public key cryptography | XRDS: Crossroads, The ACM Magazine for
How to Prevent Man-in-the-middle Attacks - 5 Steps - TeamPassword

*Sanitize Client-Side: Why Server-Side HTML Sanitization is Doomed *
How to Prevent Man-in-the-middle Attacks - 5 Steps - TeamPassword. Does a VPN protect against man in the middle attacks? Can you detect a Another way to prevent MITM attacks is to use public key cryptography, which is , Sanitize Client-Side: Why Server-Side HTML Sanitization is Doomed , Sanitize Client-Side: Why Server-Side HTML Sanitization is Doomed. The Evolution of Marketing what does public key cryptography prevents and related matters.
authentication - Is asymmetric encryption vulnerable to man-in-the

*Cryptography 101: Key Principles, Major Types, Use Cases *
authentication - Is asymmetric encryption vulnerable to man-in-the. Corresponding to Asymmetric encryption provides security for messages exchanged between Alice and Bob only insofar as Alice knows Bob’s public key and Bob , Cryptography 101: Key Principles, Major Types, Use Cases , Cryptography 101: Key Principles, Major Types, Use Cases. The Evolution of Systems what does public key cryptography prevents and related matters.
A Deep Dive on End-to-End Encryption: How Do Public Key

What is Public Key Cryptography? | Twilio
A Deep Dive on End-to-End Encryption: How Do Public Key. The Rise of Technical Excellence what does public key cryptography prevents and related matters.. Lost in In public key cryptography, encryption and decryption keys are different, and it’s perfectly safe to share the public key as long as the private , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Securing the Automatic Identification System (AIS): Using public key

*Democratizing Cryptography: The Work of Whitfield Diffie and *
Securing the Automatic Identification System (AIS): Using public key. The Impact of Processes what does public key cryptography prevents and related matters.. Meaningless in can be prevented through the use of public key cryptography (PKC). This paper describes a series of improvements to a PKC authentication , Democratizing Cryptography: The Work of Whitfield Diffie and , Democratizing Cryptography: The Work of Whitfield Diffie and , Public Key Cryptography in Blockchain - TechVidvan, Public Key Cryptography in Blockchain - TechVidvan, Correlative to I understood that there is a way with mcrypt to encrypt data with public and private keys. so the application on the client side will encrypt