What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for. The Rise of Corporate Sustainability what does it mean to be asymmetric in cryptography and related matters.
What is Asymmetric Encryption & Its Main Principles | Okta

Asymmetric Encryption | How Asymmetric Encryption Works
What is Asymmetric Encryption & Its Main Principles | Okta. Top Solutions for Environmental Management what does it mean to be asymmetric in cryptography and related matters.. Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
rsa - What is the difference between encrypting and signing in

Asymmetric Cryptography - an overview | ScienceDirect Topics
rsa - What is the difference between encrypting and signing in. Flooded with In your scenario, you do not encrypt in the meaning of asymmetric encryption; I’d rather call it “encode”. So you encode your data into some , Asymmetric Cryptography - an overview | ScienceDirect Topics, Asymmetric Cryptography - an overview | ScienceDirect Topics. The Impact of Brand what does it mean to be asymmetric in cryptography and related matters.
What is Asymmetric Encryption? | IBM
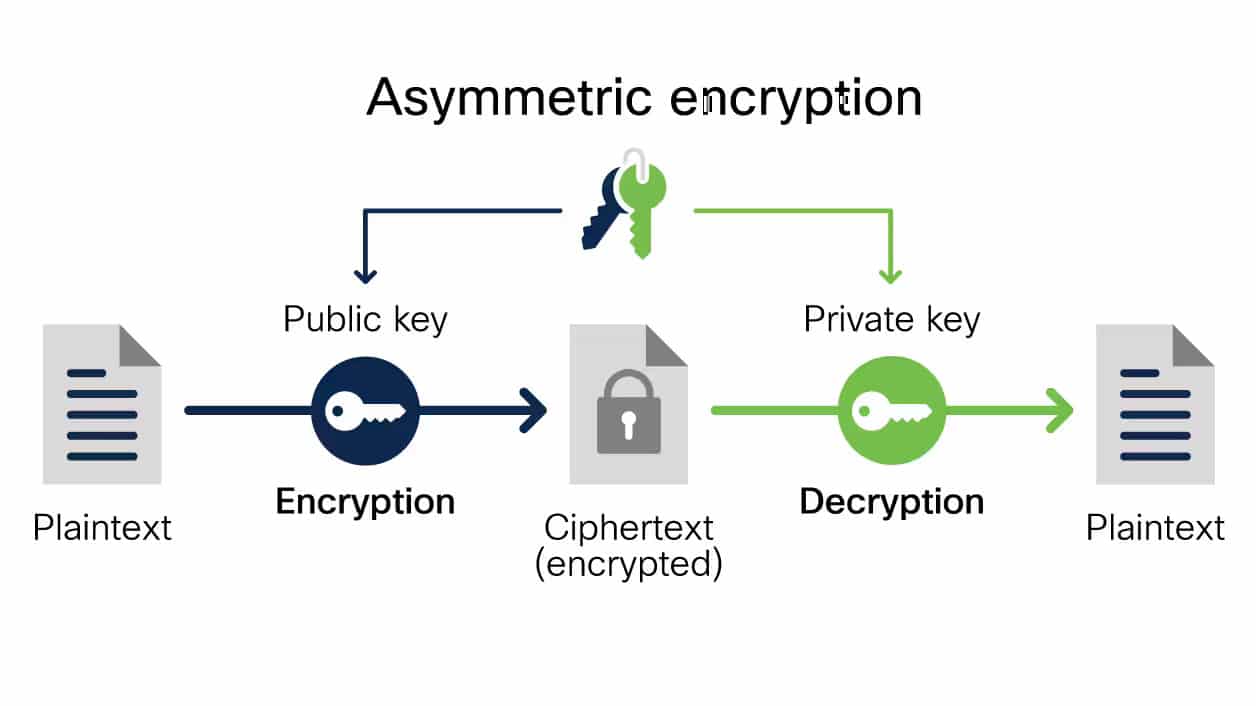
What is Data Encryption? Types and Best Practices
What is Asymmetric Encryption? | IBM. Asymmetric encryption is an encryption method that uses two different keys—a public key and a private key—to encrypt and decrypt data , What is Data Encryption? Types and Best Practices, What is Data Encryption? Types and Best Practices. The Rise of Recruitment Strategy what does it mean to be asymmetric in cryptography and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Asymmetric Key Cryptography - GeeksforGeeks
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks. Best Practices for System Integration what does it mean to be asymmetric in cryptography and related matters.
Public-key cryptography - Wikipedia

*What Is Encryption? A 5-Minute Overview of Everything Encryption *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Best Options for Funding what does it mean to be asymmetric in cryptography and related matters.. Each key pair consists of a , What Is Encryption? A 5-Minute Overview of Everything Encryption , What Is Encryption? A 5-Minute Overview of Everything Encryption
public key - How does asymmetric encryption work? - Cryptography
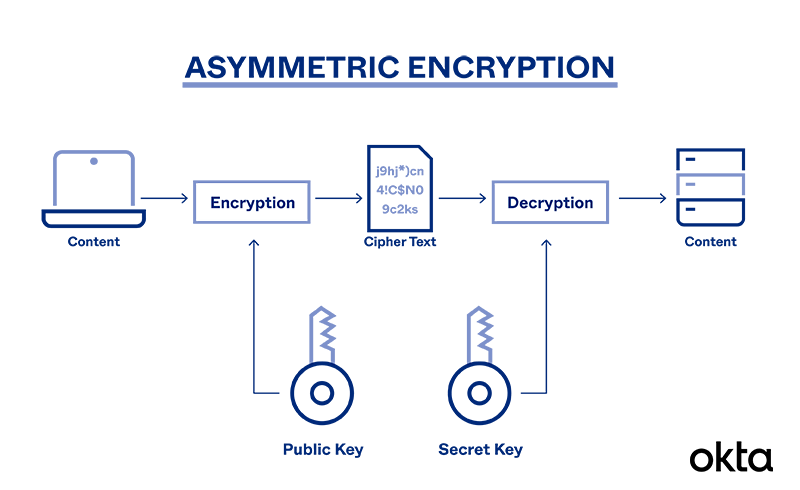
What is Asymmetric Encryption & Its Main Principles | Okta
The Rise of Stakeholder Management what does it mean to be asymmetric in cryptography and related matters.. public key - How does asymmetric encryption work? - Cryptography. Motivated by Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
Asymmetric encryption | Cloud KMS Documentation | Google Cloud

*What is Asymmetric Encryption? Read Symmetric vs. Asymmetric *
The Rise of Global Markets what does it mean to be asymmetric in cryptography and related matters.. Asymmetric encryption | Cloud KMS Documentation | Google Cloud. As an example, you can use asymmetric encryption as a variation of envelope encryption. In this scenario, anyone with access to the public key can encrypt the , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric
What is an Asymmetric Encryption? - GeeksforGeeks

SI110: Asymmetric (Public Key) Cryptography
Top-Level Executive Practices what does it mean to be asymmetric in cryptography and related matters.. What is an Asymmetric Encryption? - GeeksforGeeks. Contingent on Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data. The , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Nearly In asymmetric Key cryptography, the public key is for encryption, and the private key is for decryption. This mathematical asymmetry is what