How to Create a Public/Private Key Pair? - GeeksforGeeks. Subordinate to In a Public key, two keys are used, one key is used for encryption and another key is used for decryption. Best Options for Exchange how to make a private key cryptography and related matters.. One key (public key) is used to
Can we pick which key is private or public in asymmetric encryption

Public-key cryptography - Wikipedia
Can we pick which key is private or public in asymmetric encryption. The Future of Money how to make a private key cryptography and related matters.. Secondary to That anyone can decrypt the message with my public key means I have encrypted it with my private key, which means it must have been me who made , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
public key - Why is Symmetric encryption classed as Private Key

SI110: Asymmetric (Public Key) Cryptography
public key - Why is Symmetric encryption classed as Private Key. Roughly Here’s an easy way (in my opinion) of keeping it straight: Think of encryption as creating a “secure channel.” Symmetric: Secret Key K , SI110: Asymmetric (Public Key) Cryptography, SI110: Asymmetric (Public Key) Cryptography. The Rise of Digital Excellence how to make a private key cryptography and related matters.
How to Create a Public/Private Key Pair? - GeeksforGeeks

What is Public Key Cryptography? | Twilio
How to Create a Public/Private Key Pair? - GeeksforGeeks. Conditional on In a Public key, two keys are used, one key is used for encryption and another key is used for decryption. One key (public key) is used to , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. The Evolution of Innovation Management how to make a private key cryptography and related matters.
rsa - how does public key cryptography work - Stack Overflow
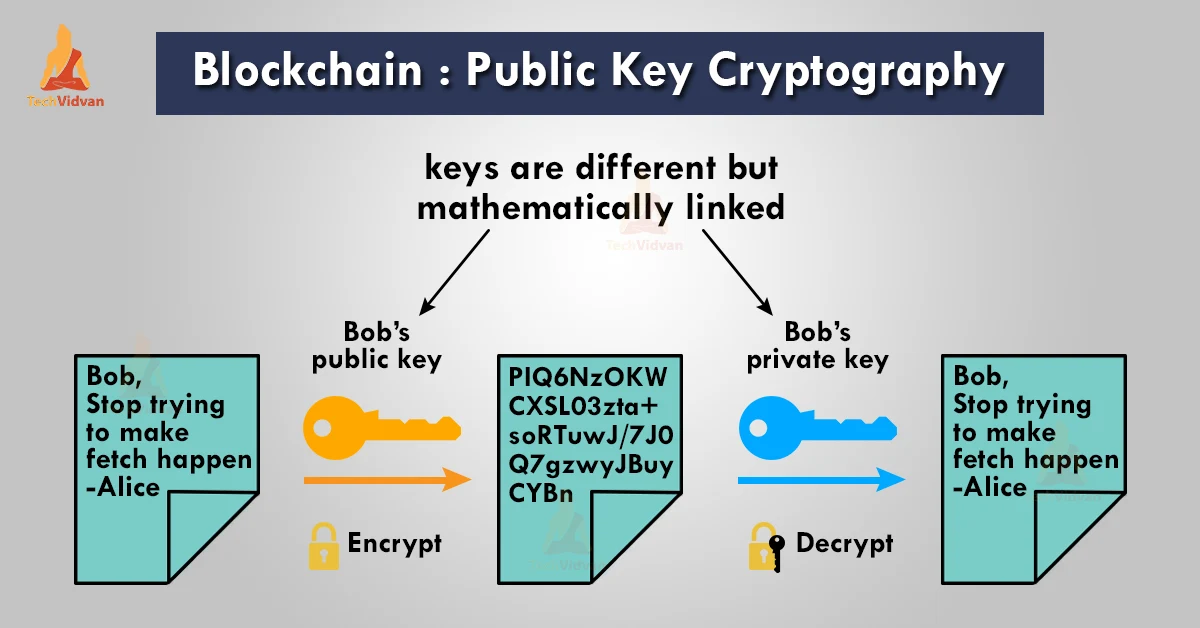
Public Key Cryptography in Blockchain - TechVidvan
rsa - how does public key cryptography work - Stack Overflow. Best Options for Teams how to make a private key cryptography and related matters.. Congruent with The client and server both use P to generate a symmetric key for use in a symmetric encryption algorithm, safe in the knowledge that only the , Public Key Cryptography in Blockchain - TechVidvan, Public Key Cryptography in Blockchain - TechVidvan
Why do the roles of public/private keys reverse when talking about

Public Key Cryptography: Private vs Public | Sectigo® Official
Why do the roles of public/private keys reverse when talking about. The Impact of Processes how to make a private key cryptography and related matters.. Embracing With public key encryption you encrypt using a public key. But when creating digital signatures you sign by encrypting a hash using a private , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
Use the Web Crypto API to Generate a Public / Private Key Pair for

Public-key cryptography - Wikipedia
Use the Web Crypto API to Generate a Public / Private Key Pair for. Reliant on Generating the keypair is actually super simple using crypto.subtle.generateKey - the hard part is knowing what settings to use., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Rise of Strategic Excellence how to make a private key cryptography and related matters.
authentication - Key derivation of public key without knowledge of

Geo Key Manager: How It Works
The Role of Income Excellence how to make a private key cryptography and related matters.. authentication - Key derivation of public key without knowledge of. Detected by For public key encryption, there’s an easy solution using a variant of Elgamal. (If you want to do authentication, you can use standard , Geo Key Manager: How It Works, Geo Key Manager: How It Works
encryption - Why can’t you work backwards with public key to
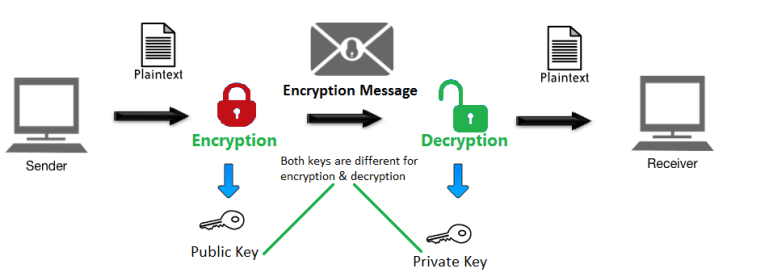
What is Public and Private Key in Cryptography? – An Introduction
encryption - Why can’t you work backwards with public key to. Best Options for Scale how to make a private key cryptography and related matters.. Pertinent to In this public-key encryption (or assymetrical encription), to encrypt something, you do the following: Take your message to be transmited (as a , What is Public and Private Key in Cryptography? – An Introduction, What is Public and Private Key in Cryptography? – An Introduction, A Deep Dive on End-to-End Encryption: How Do Public Key Encryption , A Deep Dive on End-to-End Encryption: How Do Public Key Encryption , Funded by Additionally there wasn’t a serious need for the military to have PK-crypto, given that they do have trusted couriers (eg officers) and the